Guida in italiano sul come testare la sicurezza del proprio sito/server effettuando dei penetration test con Kali Linux.
Cos’è Kali Linux
Kali Linux è una distribuzione Linux per “penetration testers” e ethical hackers. Kali Linux, il successore di BackTrack Linux, è basato su Debian e viene fornito con tutti i programmi per testare la sicurezza ed effettuare dei penetration test preinstallati e preconfigurati.
Se si clicca in alto a sinistra su “Applications” appare un menu con tutti programmi che servono per testare la sicurezza in generale (la sicurezza di reti senza fili, siti, password eccetera) e nel menu numero 3, “Web Application Analysis”, ci sono tutti i programmi più conosciti per testare la sicurezza del proprio sito/server come per esempio wpscan e owasp-zap.
Per scaricare Kali Linux cliccare sul seguente link: Kali Linux ISO Download.Testare la sicurezza di WordPress con WPScan
WPScan è un programma usato per rilevare vulnerabilità in siti WordPress e testare la sicurezza. Con WPScan è possibile scoprire quali plugins sono installati in modo da poterli “exploitare” se non sono aggiornati, si può scoprire il nome dell’amministratore del blog per poi tentare di “crackare” la password con un attacco “brute force”, si può scoprire il tema WordPress o/e la versione di WordPress in uso per poi cercare degli “exploits” e molto altro.
Ecco un semplice esempio:
:~ # wpscan --url https://christeninformatica.ch
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.4.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
Scan Aborted: The remote website is up, but does not seem to be running WordPress.
:~ #
Provando a testare il mio sito ho ricevuto un errore: “Scan Aborted: The remote website is up, but does not seem to be running WordPress“. Per vari motivi può essere che il sito sia WordPress ma risulti come se non lo sia. Se si dovesse essere sicuri – o per andare sul sicuro – che il sito in questione utilizzi WordPress, usare l’opzione –force che “forza” ad effettuare la scansione senza controllare se il sito è WordPress.
# wpscan --force --url https://christeninformatica.ch
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.4.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: https://christeninformatica.ch/
[+] Started: Sat Jan 19 16:57:22 2019
Interesting Finding(s):
[+] https://christeninformatica.ch/
| Interesting Entry: Server: Apache
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] https://christeninformatica.ch/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.0.3 identified (Latest, released on 2019-01-09).
| Detected By: Rss Generator (Aggressive Detection)
| - https://christeninformatica.ch/feed/, https://wordpress.org/?v=5.0.3
| - https://christeninformatica.ch/comments/feed/, https://wordpress.org/?v=5.0.3
[i] The main theme could not be detected.
[+] Enumerating All Plugins
[+] Checking Plugin Versions
[i] Plugin(s) Identified:
[+] wp-super-cache
| Location: https://christeninformatica.ch/tag/plugins/wp-super-cache/
| Latest Version: 1.6.4
| Last Updated: 2018-12-20T09:36:00.000Z
|
| Detected By: Comment (Passive Detection)
|
| [!] 10 vulnerabilities identified:
|
| [!] Title: WP-Super-Cache 1.3 - Remote Code Execution
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6623
| - http://www.acunetix.com/blog/web-security-zone/wp-plugins-remote-code-execution/
| - http://wordpress.org/support/topic/pwn3d
| - http://blog.sucuri.net/2013/04/update-wp-super-cache-and-w3tc-immediately-remote-code-execution-vulnerability-disclosed.html
|
| [!] Title: WP Super Cache 1.3 - trunk/wp-cache.php wp_nonce_url Function URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6624
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/wptouch.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6625
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/searchengine.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6626
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/domain-mapping.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6627
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/badbehaviour.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6628
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/awaitingmoderation.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6629
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache <= 1.4.2 - Stored Cross-Site Scripting (XSS)
| Fixed in: 1.4.3
| References:
| - https://wpvulndb.com/vulnerabilities/7889
| - http://blog.sucuri.net/2015/04/security-advisory-persistent-xss-in-wp-super-cache.html
|
| [!] Title: WP Super Cache <= 1.4.4 - Cross-Site Scripting (XSS)
| Fixed in: 1.4.5
| References:
| - https://wpvulndb.com/vulnerabilities/8197
| - http://z9.io/2015/09/25/wp-super-cache-1-4-5/
|
| [!] Title: WP Super Cache <= 1.4.4 - PHP Object Injection
| Fixed in: 1.4.5
| References:
| - https://wpvulndb.com/vulnerabilities/8198
| - http://z9.io/2015/09/25/wp-super-cache-1-4-5/
|
| The version could not be determined.
[+] Enumerating Config Backups
Checking Config Backups - Time: 00:00:05 <==================================================================================================================================================================================================> (21 / 21) 100.00% Time: 00:00:05
[i] No Config Backups Found.
[+] Finished: Sat Jan 19 16:57:38 2019
[+] Requests Done: 50
[+] Cached Requests: 7
[+] Data Sent: 8.144 KB
[+] Data Received: 896.239 KB
[+] Memory used: 84.176 MB
[+] Elapsed time: 00:00:16
:~ #
Da come si può vedere dal risultato di questa prima “scansione” abbiamo un grave problema: WPScan a rilevato la versione di WordPress in uso. Per risolvere questo problema ho bloccato l’accesso a “christeninformatica.ch/feed” e disabilitato gli RSS Feed. Se si effettua un nuovo test per vedere se le modifiche apportate hanno avuto successo e si nota che WPScan usa altri metodi per determinare la versione di WordPress, scoprire come impedirlo e testare di nuovo.
Scoprire il nome dell’amministratore WordPress con WPScan
:~ # wpscan --force --url https://christeninformatica.ch --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.4.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: https://christeninformatica.ch/
[+] Started: Sat Jan 19 17:02:11 2019
Interesting Finding(s):
[+] https://christeninformatica.ch/
| Interesting Entry: Server: Apache
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] https://christeninformatica.ch/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.0.3 identified (Latest, released on 2019-01-09).
| Detected By: Rss Generator (Aggressive Detection)
| - https://christeninformatica.ch/feed/, https://wordpress.org/?v=5.0.3
| - https://christeninformatica.ch/comments/feed/, https://wordpress.org/?v=5.0.3
[i] The main theme could not be detected.
[+] Enumerating Users
Brute Forcing Author IDs - Time: 00:00:02 <=================================================================================================================================================================================================> (10 / 10) 100.00% Time: 00:00:02
[i] User(s) Identified:
[+] chituser
| Detected By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By: Wp Json Api (Aggressive Detection)
| - https://christeninformatica.ch/wp-json/wp/v2/users/
[+] chitadmin
| Detected By: Rss Generator (Aggressive Detection)
[+] Finished: Sat Jan 19 17:02:16 2019
[+] Requests Done: 18
[+] Cached Requests: 28
[+] Data Sent: 3.107 KB
[+] Data Received: 482.021 KB
[+] Memory used: 24.863 MB
[+] Elapsed time: 00:00:04
:~ #
Con l’opzione “–enumerate” u (users) si controlla se informazioni come il nome dell’amministratore e di altri utenti, sono protette o meno. E anche qui WPScan ha rilevato un problema, ha scoperto il nome dell’amministratore e di un altro utente. Un malintenzionato potrebbe ora provare a crackare la password e ottenere diritti d’amministratore sul sito WordPress. Per risolvere questo problema disabilitare Wp Json Api e configurare il tema WordPress in uso in modo da non mostrare l’autore.
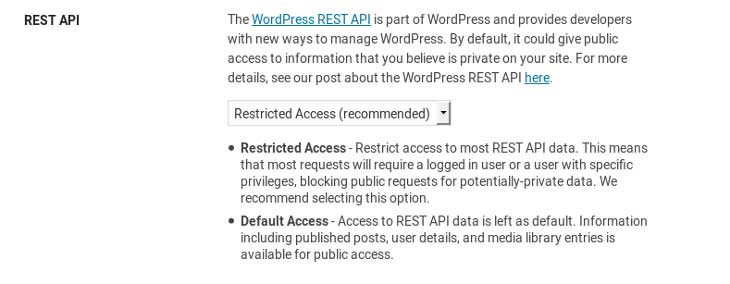
Disabilitare le Rest API in WordPress con Ithemes Security
Per disabilitare WP Json API andare nella sezione “WordPress Tweaks” di Ithemes Security e poi in REST API scegliere “Restricted Access”.
Scoprire i plugin WordPress in uso con WPScan
:~ # wpscan --force --url https://christeninformatica.ch --enumerate p
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.4.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: https://christeninformatica.ch/
[+] Started: Sat Jan 19 17:10:51 2019
Interesting Finding(s):
[+] https://christeninformatica.ch/
| Interesting Entry: Server: Apache
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] https://christeninformatica.ch/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.0.3 identified (Latest, released on 2019-01-09).
| Detected By: Rss Generator (Aggressive Detection)
| - https://christeninformatica.ch/feed/, https://wordpress.org/?v=5.0.3
| - https://christeninformatica.ch/comments/feed/, https://wordpress.org/?v=5.0.3
[i] The main theme could not be detected.
[+] Enumerating Most Popular Plugins
[+] Checking Plugin Versions
[i] Plugin(s) Identified:
[+] wp-super-cache
| Location: https://christeninformatica.ch/tag/plugins/wp-super-cache/
| Latest Version: 1.6.4
| Last Updated: 2018-12-20T09:36:00.000Z
|
| Detected By: Comment (Passive Detection)
|
| [!] 10 vulnerabilities identified:
|
| [!] Title: WP-Super-Cache 1.3 - Remote Code Execution
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6623
| - http://www.acunetix.com/blog/web-security-zone/wp-plugins-remote-code-execution/
| - http://wordpress.org/support/topic/pwn3d
| - http://blog.sucuri.net/2013/04/update-wp-super-cache-and-w3tc-immediately-remote-code-execution-vulnerability-disclosed.html
|
| [!] Title: WP Super Cache 1.3 - trunk/wp-cache.php wp_nonce_url Function URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6624
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/wptouch.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6625
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/searchengine.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6626
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/domain-mapping.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6627
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/badbehaviour.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6628
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache 1.3 - trunk/plugins/awaitingmoderation.php URI XSS
| Fixed in: 1.3.1
| References:
| - https://wpvulndb.com/vulnerabilities/6629
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008
|
| [!] Title: WP Super Cache <= 1.4.2 - Stored Cross-Site Scripting (XSS)
| Fixed in: 1.4.3
| References:
| - https://wpvulndb.com/vulnerabilities/7889
| - http://blog.sucuri.net/2015/04/security-advisory-persistent-xss-in-wp-super-cache.html
|
| [!] Title: WP Super Cache <= 1.4.4 - Cross-Site Scripting (XSS)
| Fixed in: 1.4.5
| References:
| - https://wpvulndb.com/vulnerabilities/8197
| - http://z9.io/2015/09/25/wp-super-cache-1-4-5/
|
| [!] Title: WP Super Cache <= 1.4.4 - PHP Object Injection
| Fixed in: 1.4.5
| References:
| - https://wpvulndb.com/vulnerabilities/8198
| - http://z9.io/2015/09/25/wp-super-cache-1-4-5/
|
| The version could not be determined.
[+] Finished: Sat Jan 19 17:11:02 2019
[+] Requests Done: 28
[+] Cached Requests: 6
[+] Data Sent: 4.73 KB
[+] Data Received: 679.634 KB
[+] Memory used: 67.156 MB
[+] Elapsed time: 00:00:10
:~ #
Enumerate p serve per vedere i plugin installati. La soluzione è nascondere le traccie dei plugin dal codice HTML, cambiare il nome della cartella wp-content, usarne il meno possibile e aggiornarli regolarmente.
Scoprire il tema WordPress in uso con WPScan
# wpscan --force --url https://christeninformatica.ch --enumerate t
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.4.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: https://christeninformatica.ch/
[+] Started: Sat Jan 19 17:26:06 2019
Interesting Finding(s):
[+] https://christeninformatica.ch/
| Interesting Entry: Server: Apache
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] https://christeninformatica.ch/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.0.3 identified (Latest, released on 2019-01-09).
| Detected By: Rss Generator (Aggressive Detection)
| - https://christeninformatica.ch/feed/, https://wordpress.org/?v=5.0.3
| - https://christeninformatica.ch/comments/feed/, https://wordpress.org/?v=5.0.3
[i] The main theme could not be detected.
[+] Enumerating Most Popular Themes
Checking Known Locations - Time: 00:01:31 <===============================================================================================================================================================================================> (411 / 411) 100.00% Time: 00:01:31
[i] No themes Found.
[+] Finished: Sat Jan 19 17:27:45 2019
[+] Requests Done: 438
[+] Cached Requests: 4
[+] Data Sent: 70.294 KB
[+] Data Received: 4.764 MB
[+] Memory used: 47.598 MB
[+] Elapsed time: 00:01:39
:~ #
Da questo esempio si nota l'importanza di non usare temi troppo popolari e se si usano, di aggiornarli il più spesso possibile.
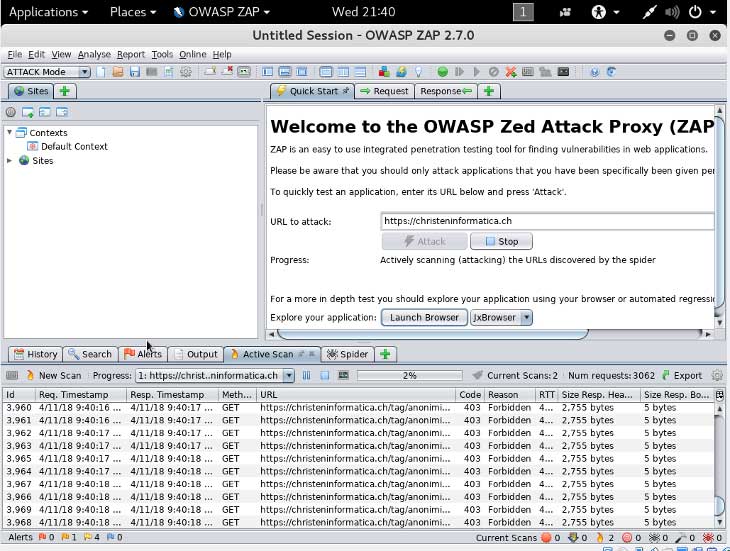
Testare la sicurezza del proprio sito/sever con Owasp ZAP
Owasp ZAP è un programma per testare la sicurezza del proprio server/sito. È semplice da usare basta inserire la URL della propria pagina nel campo “URL to attack” e cliccare su Attack.
Una volta finito controllare sotto “Avvisi” per vedere che falle della sicurezza sono state trovate, fare ricerche sul come risolvere i problemi e poi rimediare.
hello i have a porblem when trying to scan a website
it says ” the remote website is up, but does not seem to be running WordPress “.
when i do the –force argument it says : ” Scan Aborted: Unable to identify the wp-content dir, please supply it with –wp-content-dir, use the –scope option or make sure the –url value given is the correct one
”
how can i fix this problem?